Are you over 18 and want to see adult content?
More Annotations
A complete backup of www.mediasetplay.mediaset.it/article/chivuolesseremilionario/chi-e-la-donna-piu-bella-del-2019-secondo-peop
Are you over 18 and want to see adult content?
A complete backup of www.spiegel.de/sport/fussball/champions-league-real-madrid-vs-manchester-city-real-graetscht-sich-an-den-ab
Are you over 18 and want to see adult content?
A complete backup of www.spiegel.de/sport/fussball/lucas-tousart-schiesst-olympique-lyon-gegen-juventus-in-der-champions-league-
Are you over 18 and want to see adult content?
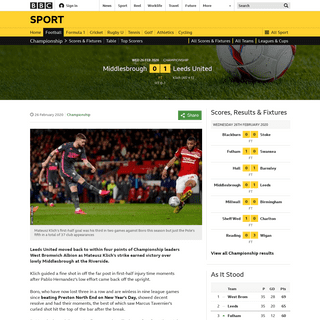
A complete backup of www.bbc.co.uk/sport/football/51533048
Are you over 18 and want to see adult content?
Favourite Annotations

DIXIE MIDDLE SCHOOL SCIENCE - Dixie Middle Science
Are you over 18 and want to see adult content?
Vse za zdravje in o zdravju - Zdravje.online
Are you over 18 and want to see adult content?
TRUVADA for PrEP® (Pre-Exposure Prophylaxis)
Are you over 18 and want to see adult content?

Body by Design - Home - Aberden,, SD
Are you over 18 and want to see adult content?

Okna Łódź BUDVAR. Drzwi Okna PCV, Aluminiowe, Drewniane w Łodzi
Are you over 18 and want to see adult content?
A complete backup of jaypeejournals.com
Are you over 18 and want to see adult content?
Celebrations of Life – past, present, and future
Are you over 18 and want to see adult content?
Text
so keep on updates.
INFORMATION TECHNOLOGY GEMS: COMPUTER SCIENCE MILESTONES Computer Science Milestones (1900 - 2011) I wanted to share with you a timeline of major events in computer science history. The milestones listed hereunder are those that I deem important and include only 20th and 21st century events. 1900 - In a lecture to the International Congress of Mathematicians, David Hilbert asks for way to mechanize INFORMATION TECHNOLOGY GEMS: SETS, BAGS AND SEQUENCES A sequence is an ordered bag. To distinguish ordered sequences from unordered sets and bags, the elements of a sequence are enclosed in angle brackets: 178, 184, 178, 181; the empty sequence is written . If a sequence has n elements, the elements are numbered from 1 to n (or alternatively from 0 to n-1). A sequence of two elements is sometimes INFORMATION TECHNOLOGY GEMS: COMPUTER ARCHITECTURES One way of categorizing computer architectures is by number of instructions executed per clock. Many computing machines read one instruction at a time and execute it (or they put a lot of effort into acting as if they do that, even if internally they do fancy superscalar and out-of-order stuff). I call such machines "von Neumann" machines, because all of them have a von Neumann bottleneck. INFORMATION TECHNOLOGY GEMS: USING FIND AND GREP Whether searching through source code or log files, the ability to display the surrounding lines is often useful. For example: $ grep -r -A 2 foo src. will display the lines that contain foo and the two subsequent lines. Similarly, you can use. -B b efore. -C c entered (lines both before and after found text.) INFORMATION TECHNOLOGY GEMS: 2011 The Product Backlog is a list of functional and nonfunctional requirements that, when turned into functionality, will deliver this vision. The Product Backlog is prioritized so that the items most likely to generate value are top priority and is divided into proposed releases.The prioritized Product Backlog is a starting point, and the contents, priorities, and grouping of the Product Backlog INFORMATION TECHNOLOGY GEMS: 10 FREQUENTLY USED UNIX This short post provides practical examples for ten most frequently used commands in Linux/UNIX. The purpose of this list is to give you a jump-start on some of the common Linux commands. INFORMATION TECHNOLOGY GEMS: SEPTEMBER 2011 The fundamental interface to an Oracle database is an Oracle command-line utility program called SQL*Plus.This utility is available at every Oracle site INFORMATION TECHNOLOGY GEMS DNS information is stored on every individual’s computer via DNS Client Service (Microsoft Windows) into the Operating System cache. 2. Browsers Cache. Many of the browsers allow for storing cache, As long as the cached data is remain inside the browser there INFORMATION TECHNOLOGY GEMS: DESIGN PATTERNS Example 1: As shareholders in a company, you can either go to a meeting and vote, or you can place a proxy vote. The proxy vote is handled by an intermediary, but represents the actual vote. Example 2: Remote interfaces in EJB and Java’s RMI implementation. The next pattern set is referred to as Behavioral patterns. INFORMATION TECHNOLOGY GEMS: JAVA COLLECTIONS All are saying the same thing repeatedly, but in your blog I had a chance to get some useful and unique information, I love your writing style very much, I would like to suggest your blog in my dude circle,so keep on updates.
INFORMATION TECHNOLOGY GEMS: COMPUTER SCIENCE MILESTONES Computer Science Milestones (1900 - 2011) I wanted to share with you a timeline of major events in computer science history. The milestones listed hereunder are those that I deem important and include only 20th and 21st century events. 1900 - In a lecture to the International Congress of Mathematicians, David Hilbert asks for way to mechanize INFORMATION TECHNOLOGY GEMS: SETS, BAGS AND SEQUENCES A sequence is an ordered bag. To distinguish ordered sequences from unordered sets and bags, the elements of a sequence are enclosed in angle brackets: 178, 184, 178, 181; the empty sequence is written . If a sequence has n elements, the elements are numbered from 1 to n (or alternatively from 0 to n-1). A sequence of two elements is sometimes INFORMATION TECHNOLOGY GEMS: COMPUTER ARCHITECTURES One way of categorizing computer architectures is by number of instructions executed per clock. Many computing machines read one instruction at a time and execute it (or they put a lot of effort into acting as if they do that, even if internally they do fancy superscalar and out-of-order stuff). I call such machines "von Neumann" machines, because all of them have a von Neumann bottleneck. INFORMATION TECHNOLOGY GEMS: USING FIND AND GREP Whether searching through source code or log files, the ability to display the surrounding lines is often useful. For example: $ grep -r -A 2 foo src. will display the lines that contain foo and the two subsequent lines. Similarly, you can use. -B b efore. -C c entered (lines both before and after found text.) INFORMATION TECHNOLOGY GEMS: 2011 The Product Backlog is a list of functional and nonfunctional requirements that, when turned into functionality, will deliver this vision. The Product Backlog is prioritized so that the items most likely to generate value are top priority and is divided into proposed releases.The prioritized Product Backlog is a starting point, and the contents, priorities, and grouping of the Product Backlog INFORMATION TECHNOLOGY GEMS: 10 FREQUENTLY USED UNIX This short post provides practical examples for ten most frequently used commands in Linux/UNIX. The purpose of this list is to give you a jump-start on some of the common Linux commands. INFORMATION TECHNOLOGY GEMS: SEPTEMBER 2011 The fundamental interface to an Oracle database is an Oracle command-line utility program called SQL*Plus.This utility is available at every Oracle site INFORMATION TECHNOLOGY GEMS: USING FIND AND GREP Whether searching through source code or log files, the ability to display the surrounding lines is often useful. For example: $ grep -r -A 2 foo src. will display the lines that contain foo and the two subsequent lines. Similarly, you can use. -B b efore. -C c entered (lines both before and after found text.) INFORMATION TECHNOLOGY GEMS: VI ESSENTIALS Sometimes you visit a client and you have got only access to the vi editor.While this editor can be frustrating to learn especially for Windows and Mac users I believe that learning or referring to the below commands might become handy to any IT professional. INFORMATION TECHNOLOGY GEMS: ORACLE SQL*PLUS ESSENTIALS The fundamental interface to an Oracle database is an Oracle command-line utility program called SQL*Plus.This utility is available at every Oracle site INFORMATION TECHNOLOGY GEMS: CHRONOLOGY OF ARTIFICIAL Logic Theorist, the first AI program, was written by Allen Newell, Herbert Simon, and J.C. Shaw. It proved theorems using a combination of searching, goal-oriented behavior, and INFORMATION TECHNOLOGY GEMS: DECEMBER 2011 The Product Backlog is a list of functional and nonfunctional requirements that, when turned into functionality, will deliver this vision. The Product Backlog is prioritized so that the items most likely to generate value are top priority and is divided into proposed releases.The prioritized Product Backlog is a starting point, and the contents, priorities, and grouping of the Product Backlog INFORMATION TECHNOLOGY GEMS: SEPTEMBER 2011 The fundamental interface to an Oracle database is an Oracle command-line utility program called SQL*Plus.This utility is available at every Oracle site INFORMATION TECHNOLOGY GEMS: OCTOBER 2011 Example 1: The "check" at a diner is an example of a Command pattern.The waiter or waitress takes an order, or command from a customer, and encapsulates that order by writing it on the check. The order is then queued for a short order cook. INFORMATION TECHNOLOGY GEMS: TASTE OF PYTHON POWER Python is a programming language that lets you work more quickly and integrate your systems more effectively. You can learn to use Python and see almost immediate gains in productivity and lower maintenancecosts.
INFORMATION TECHNOLOGY GEMS: JANUARY 2012 Python is a programming language that lets you work more quickly and integrate your systems more effectively. You can learn to use Python and see almost immediate gains in productivity and lower maintenancecosts.
INFORMATION TECHNOLOGY GEMS: PRACTICAL CRYPTOGRAPHY IN 2011 SecurID not so secure after all. RSA's SecurID has become practically synonymous with two-factor authentication. And it's not a bad system. Back in 2010 if you'd asked me about the most likely avenue for a compromise, I would have guessed (a) theft of secrets from a local SecurID server, or (b) some kind of bug in the authentication software. What I wouldn't have guessed was (c) compromise of INFORMATION TECHNOLOGY GEMS DNS information is stored on every individual’s computer via DNS Client Service (Microsoft Windows) into the Operating System cache. 2. Browsers Cache. Many of the browsers allow for storing cache, As long as the cached data is remain inside the browser there INFORMATION TECHNOLOGY GEMS: DESIGN PATTERNS Example 1: As shareholders in a company, you can either go to a meeting and vote, or you can place a proxy vote. The proxy vote is handled by an intermediary, but represents the actual vote. Example 2: Remote interfaces in EJB and Java’s RMI implementation. The next pattern set is referred to as Behavioral patterns. INFORMATION TECHNOLOGY GEMS: COMPUTER SCIENCE MILESTONES Computer Science Milestones (1900 - 2011) I wanted to share with you a timeline of major events in computer science history. The milestones listed hereunder are those that I deem important and include only 20th and 21st century events. 1900 - In a lecture to the International Congress of Mathematicians, David Hilbert asks for way to mechanize INFORMATION TECHNOLOGY GEMS: JAVA COLLECTIONS All are saying the same thing repeatedly, but in your blog I had a chance to get some useful and unique information, I love your writing style very much, I would like to suggest your blog in my dude circle,so keep on updates.
INFORMATION TECHNOLOGY GEMS: SETS, BAGS AND SEQUENCES A sequence is an ordered bag. To distinguish ordered sequences from unordered sets and bags, the elements of a sequence are enclosed in angle brackets: 178, 184, 178, 181; the empty sequence is written . If a sequence has n elements, the elements are numbered from 1 to n (or alternatively from 0 to n-1). A sequence of two elements is sometimes INFORMATION TECHNOLOGY GEMS: SCRUM FLOW The Product Backlog is a list of functional and nonfunctional requirements that, when turned into functionality, will deliver this vision. The Product Backlog is prioritized so that the items most likely to generate value are top priority and is divided into proposed releases.The prioritized Product Backlog is a starting point, and the contents, priorities, and grouping of the Product Backlog INFORMATION TECHNOLOGY GEMS: USING FIND AND GREP Whether searching through source code or log files, the ability to display the surrounding lines is often useful. For example: $ grep -r -A 2 foo src. will display the lines that contain foo and the two subsequent lines. Similarly, you can use. -B b efore. -C c entered (lines both before and after found text.) INFORMATION TECHNOLOGY GEMS: 2011 The Product Backlog is a list of functional and nonfunctional requirements that, when turned into functionality, will deliver this vision. The Product Backlog is prioritized so that the items most likely to generate value are top priority and is divided into proposed releases.The prioritized Product Backlog is a starting point, and the contents, priorities, and grouping of the Product Backlog INFORMATION TECHNOLOGY GEMS: 10 FREQUENTLY USED UNIX This short post provides practical examples for ten most frequently used commands in Linux/UNIX. The purpose of this list is to give you a jump-start on some of the common Linux commands. INFORMATION TECHNOLOGY GEMS: SEPTEMBER 2011 The fundamental interface to an Oracle database is an Oracle command-line utility program called SQL*Plus.This utility is available at every Oracle site INFORMATION TECHNOLOGY GEMS DNS information is stored on every individual’s computer via DNS Client Service (Microsoft Windows) into the Operating System cache. 2. Browsers Cache. Many of the browsers allow for storing cache, As long as the cached data is remain inside the browser there INFORMATION TECHNOLOGY GEMS: DESIGN PATTERNS Example 1: As shareholders in a company, you can either go to a meeting and vote, or you can place a proxy vote. The proxy vote is handled by an intermediary, but represents the actual vote. Example 2: Remote interfaces in EJB and Java’s RMI implementation. The next pattern set is referred to as Behavioral patterns. INFORMATION TECHNOLOGY GEMS: COMPUTER SCIENCE MILESTONES Computer Science Milestones (1900 - 2011) I wanted to share with you a timeline of major events in computer science history. The milestones listed hereunder are those that I deem important and include only 20th and 21st century events. 1900 - In a lecture to the International Congress of Mathematicians, David Hilbert asks for way to mechanize INFORMATION TECHNOLOGY GEMS: JAVA COLLECTIONS All are saying the same thing repeatedly, but in your blog I had a chance to get some useful and unique information, I love your writing style very much, I would like to suggest your blog in my dude circle,so keep on updates.
INFORMATION TECHNOLOGY GEMS: SETS, BAGS AND SEQUENCES A sequence is an ordered bag. To distinguish ordered sequences from unordered sets and bags, the elements of a sequence are enclosed in angle brackets: 178, 184, 178, 181; the empty sequence is written . If a sequence has n elements, the elements are numbered from 1 to n (or alternatively from 0 to n-1). A sequence of two elements is sometimes INFORMATION TECHNOLOGY GEMS: SCRUM FLOW The Product Backlog is a list of functional and nonfunctional requirements that, when turned into functionality, will deliver this vision. The Product Backlog is prioritized so that the items most likely to generate value are top priority and is divided into proposed releases.The prioritized Product Backlog is a starting point, and the contents, priorities, and grouping of the Product Backlog INFORMATION TECHNOLOGY GEMS: USING FIND AND GREP Whether searching through source code or log files, the ability to display the surrounding lines is often useful. For example: $ grep -r -A 2 foo src. will display the lines that contain foo and the two subsequent lines. Similarly, you can use. -B b efore. -C c entered (lines both before and after found text.) INFORMATION TECHNOLOGY GEMS: 2011 The Product Backlog is a list of functional and nonfunctional requirements that, when turned into functionality, will deliver this vision. The Product Backlog is prioritized so that the items most likely to generate value are top priority and is divided into proposed releases.The prioritized Product Backlog is a starting point, and the contents, priorities, and grouping of the Product Backlog INFORMATION TECHNOLOGY GEMS: 10 FREQUENTLY USED UNIX This short post provides practical examples for ten most frequently used commands in Linux/UNIX. The purpose of this list is to give you a jump-start on some of the common Linux commands. INFORMATION TECHNOLOGY GEMS: SEPTEMBER 2011 The fundamental interface to an Oracle database is an Oracle command-line utility program called SQL*Plus.This utility is available at every Oracle site INFORMATION TECHNOLOGY GEMS: USING FIND AND GREP Whether searching through source code or log files, the ability to display the surrounding lines is often useful. For example: $ grep -r -A 2 foo src. will display the lines that contain foo and the two subsequent lines. Similarly, you can use. -B b efore. -C c entered (lines both before and after found text.) INFORMATION TECHNOLOGY GEMS: OOP FEATURES AND PRINCIPLES Encapsulation refers to the creation of self-contained modules that bind processing functions to the data. These user-defined data types are called "classes," and one instance of a INFORMATION TECHNOLOGY GEMS: VI ESSENTIALS Sometimes you visit a client and you have got only access to the vi editor.While this editor can be frustrating to learn especially for Windows and Mac users I believe that learning or referring to the below commands might become handy to any IT professional. INFORMATION TECHNOLOGY GEMS: SEPTEMBER 2011 The fundamental interface to an Oracle database is an Oracle command-line utility program called SQL*Plus.This utility is available at every Oracle site INFORMATION TECHNOLOGY GEMS: OCTOBER 2011 Example 1: The "check" at a diner is an example of a Command pattern.The waiter or waitress takes an order, or command from a customer, and encapsulates that order by writing it on the check. The order is then queued for a short order cook. INFORMATION TECHNOLOGY GEMS: CHRONOLOGY OF ARTIFICIAL Logic Theorist, the first AI program, was written by Allen Newell, Herbert Simon, and J.C. Shaw. It proved theorems using a combination of searching, goal-oriented behavior, and INFORMATION TECHNOLOGY GEMS: NETWORK UTILITIES Most of the available networking tools are specialized and are mainly of interest to professionals who are maintaining a large network. Many, however are relevant to the Internet and some of these can be helpful to the average PC user. INFORMATION TECHNOLOGY GEMS: TASTE OF PYTHON POWER Python is a programming language that lets you work more quickly and integrate your systems more effectively. You can learn to use Python and see almost immediate gains in productivity and lower maintenancecosts.
INFORMATION TECHNOLOGY GEMS: AUGUST 2011 Sometimes you visit a client and you have got only access to the vi editor.While this editor can be frustrating to learn especially for Windows and Mac users I believe that learning or referring to the below commands might become handy to any IT professional. INFORMATION TECHNOLOGY GEMS Sharing ICT/InfoSec information for free in a simple, precise and hopefully enjoyable way! TheInfoTechWizard http://www.blogger.com/profile/15056544426300644318 INFORMATION TECHNOLOGY GEMS DNS information is stored on every individual’s computer via DNS Client Service (Microsoft Windows) into the Operating System cache. 2. Browsers Cache. Many of the browsers allow for storing cache, As long as the cached data is remain inside the browser there INFORMATION TECHNOLOGY GEMS: DESIGN PATTERNS Example 1: As shareholders in a company, you can either go to a meeting and vote, or you can place a proxy vote. The proxy vote is handled by an intermediary, but represents the actual vote. Example 2: Remote interfaces in EJB and Java’s RMI implementation. The next pattern set is referred to as Behavioral patterns. INFORMATION TECHNOLOGY GEMS: COMPUTER SCIENCE MILESTONES Computer Science Milestones (1900 - 2011) I wanted to share with you a timeline of major events in computer science history. The milestones listed hereunder are those that I deem important and include only 20th and 21st century events. 1900 - In a lecture to the International Congress of Mathematicians, David Hilbert asks for way to mechanize INFORMATION TECHNOLOGY GEMS: JAVA COLLECTIONS All are saying the same thing repeatedly, but in your blog I had a chance to get some useful and unique information, I love your writing style very much, I would like to suggest your blog in my dude circle,so keep on updates.
INFORMATION TECHNOLOGY GEMS: SETS, BAGS AND SEQUENCES A sequence is an ordered bag. To distinguish ordered sequences from unordered sets and bags, the elements of a sequence are enclosed in angle brackets: 178, 184, 178, 181; the empty sequence is written . If a sequence has n elements, the elements are numbered from 1 to n (or alternatively from 0 to n-1). A sequence of two elements is sometimes INFORMATION TECHNOLOGY GEMS: SCRUM FLOW The Product Backlog is a list of functional and nonfunctional requirements that, when turned into functionality, will deliver this vision. The Product Backlog is prioritized so that the items most likely to generate value are top priority and is divided into proposed releases.The prioritized Product Backlog is a starting point, and the contents, priorities, and grouping of the Product Backlog INFORMATION TECHNOLOGY GEMS: USING FIND AND GREP Whether searching through source code or log files, the ability to display the surrounding lines is often useful. For example: $ grep -r -A 2 foo src. will display the lines that contain foo and the two subsequent lines. Similarly, you can use. -B b efore. -C c entered (lines both before and after found text.) INFORMATION TECHNOLOGY GEMS: 2011 The Product Backlog is a list of functional and nonfunctional requirements that, when turned into functionality, will deliver this vision. The Product Backlog is prioritized so that the items most likely to generate value are top priority and is divided into proposed releases.The prioritized Product Backlog is a starting point, and the contents, priorities, and grouping of the Product Backlog INFORMATION TECHNOLOGY GEMS: 10 FREQUENTLY USED UNIX This short post provides practical examples for ten most frequently used commands in Linux/UNIX. The purpose of this list is to give you a jump-start on some of the common Linux commands. INFORMATION TECHNOLOGY GEMS: SEPTEMBER 2011 The fundamental interface to an Oracle database is an Oracle command-line utility program called SQL*Plus.This utility is available at every Oracle site INFORMATION TECHNOLOGY GEMS DNS information is stored on every individual’s computer via DNS Client Service (Microsoft Windows) into the Operating System cache. 2. Browsers Cache. Many of the browsers allow for storing cache, As long as the cached data is remain inside the browser there INFORMATION TECHNOLOGY GEMS: DESIGN PATTERNS Example 1: As shareholders in a company, you can either go to a meeting and vote, or you can place a proxy vote. The proxy vote is handled by an intermediary, but represents the actual vote. Example 2: Remote interfaces in EJB and Java’s RMI implementation. The next pattern set is referred to as Behavioral patterns. INFORMATION TECHNOLOGY GEMS: COMPUTER SCIENCE MILESTONES Computer Science Milestones (1900 - 2011) I wanted to share with you a timeline of major events in computer science history. The milestones listed hereunder are those that I deem important and include only 20th and 21st century events. 1900 - In a lecture to the International Congress of Mathematicians, David Hilbert asks for way to mechanize INFORMATION TECHNOLOGY GEMS: JAVA COLLECTIONS All are saying the same thing repeatedly, but in your blog I had a chance to get some useful and unique information, I love your writing style very much, I would like to suggest your blog in my dude circle,so keep on updates.
INFORMATION TECHNOLOGY GEMS: SETS, BAGS AND SEQUENCES A sequence is an ordered bag. To distinguish ordered sequences from unordered sets and bags, the elements of a sequence are enclosed in angle brackets: 178, 184, 178, 181; the empty sequence is written . If a sequence has n elements, the elements are numbered from 1 to n (or alternatively from 0 to n-1). A sequence of two elements is sometimes INFORMATION TECHNOLOGY GEMS: SCRUM FLOW The Product Backlog is a list of functional and nonfunctional requirements that, when turned into functionality, will deliver this vision. The Product Backlog is prioritized so that the items most likely to generate value are top priority and is divided into proposed releases.The prioritized Product Backlog is a starting point, and the contents, priorities, and grouping of the Product Backlog INFORMATION TECHNOLOGY GEMS: USING FIND AND GREP Whether searching through source code or log files, the ability to display the surrounding lines is often useful. For example: $ grep -r -A 2 foo src. will display the lines that contain foo and the two subsequent lines. Similarly, you can use. -B b efore. -C c entered (lines both before and after found text.) INFORMATION TECHNOLOGY GEMS: 2011 The Product Backlog is a list of functional and nonfunctional requirements that, when turned into functionality, will deliver this vision. The Product Backlog is prioritized so that the items most likely to generate value are top priority and is divided into proposed releases.The prioritized Product Backlog is a starting point, and the contents, priorities, and grouping of the Product Backlog INFORMATION TECHNOLOGY GEMS: 10 FREQUENTLY USED UNIX This short post provides practical examples for ten most frequently used commands in Linux/UNIX. The purpose of this list is to give you a jump-start on some of the common Linux commands. INFORMATION TECHNOLOGY GEMS: SEPTEMBER 2011 The fundamental interface to an Oracle database is an Oracle command-line utility program called SQL*Plus.This utility is available at every Oracle site INFORMATION TECHNOLOGY GEMS: USING FIND AND GREP Whether searching through source code or log files, the ability to display the surrounding lines is often useful. For example: $ grep -r -A 2 foo src. will display the lines that contain foo and the two subsequent lines. Similarly, you can use. -B b efore. -C c entered (lines both before and after found text.) INFORMATION TECHNOLOGY GEMS: OOP FEATURES AND PRINCIPLES Encapsulation refers to the creation of self-contained modules that bind processing functions to the data. These user-defined data types are called "classes," and one instance of a INFORMATION TECHNOLOGY GEMS: VI ESSENTIALS Sometimes you visit a client and you have got only access to the vi editor.While this editor can be frustrating to learn especially for Windows and Mac users I believe that learning or referring to the below commands might become handy to any IT professional. INFORMATION TECHNOLOGY GEMS: SEPTEMBER 2011 The fundamental interface to an Oracle database is an Oracle command-line utility program called SQL*Plus.This utility is available at every Oracle site INFORMATION TECHNOLOGY GEMS: OCTOBER 2011 Example 1: The "check" at a diner is an example of a Command pattern.The waiter or waitress takes an order, or command from a customer, and encapsulates that order by writing it on the check. The order is then queued for a short order cook. INFORMATION TECHNOLOGY GEMS: CHRONOLOGY OF ARTIFICIAL Logic Theorist, the first AI program, was written by Allen Newell, Herbert Simon, and J.C. Shaw. It proved theorems using a combination of searching, goal-oriented behavior, and INFORMATION TECHNOLOGY GEMS: NETWORK UTILITIES Most of the available networking tools are specialized and are mainly of interest to professionals who are maintaining a large network. Many, however are relevant to the Internet and some of these can be helpful to the average PC user. INFORMATION TECHNOLOGY GEMS: TASTE OF PYTHON POWER Python is a programming language that lets you work more quickly and integrate your systems more effectively. You can learn to use Python and see almost immediate gains in productivity and lower maintenancecosts.
INFORMATION TECHNOLOGY GEMS: AUGUST 2011 Sometimes you visit a client and you have got only access to the vi editor.While this editor can be frustrating to learn especially for Windows and Mac users I believe that learning or referring to the below commands might become handy to any IT professional. INFORMATION TECHNOLOGY GEMS Sharing ICT/InfoSec information for free in a simple, precise and hopefully enjoyable way! TheInfoTechWizard http://www.blogger.com/profile/15056544426300644318 INFORMATION TECHNOLOGY GEMS Sharing ICT/InfoSec information for free in a simple, precise and hopefully enjoyable way! TUESDAY, 21 FEBRUARY 2012 10 BEST PRACTICES TO SPEED UP YOUR WEBSITE Website loading speed has become the most important part of the website development from last few years. In other words the target is not only developing website but to code effectively in order to improve the response time of the website. As professional WEB DESIGN COMPANY has recommended a few essentials of how to optimize for website loading speed as mentionedbelow:
1. MAKE LOWER HTTP REQUESTS As website is composed of web elements or components like images, style sheets, scripts, Flash etc… If we tend to reduce these elements on a website it reduces the number of http requests to the server and thus in turns it increases the loading speed of the website at client’s browser. Consider the following ways to reduce the http Requests to the webserver.
INDEX
WAY
DESCRIPTION
1.
Website Design
Make a simple web design which is the best way to reduce your http requests. Simple web design reduces the number of web elements on a web page & as a response user always get small html rendered page.2.
Combined Files
Using lower amount of script files like JavaScript or CSS is the good way to increase your website loading speed. For example make a single CSS external file of the website, Compiling a code into a single file can be a challenging work but it improves the response time.3.
CSS Sprites
CSS sprites are the best way to reduce your website images requests. First combine your images into a single background image and use CSS properties like CSS-background-image and background-position properties to display the desired image segment. 2. REDUCE DNS LOOK UPS DNS stands for Domain Name System. It is the concept used for the URL resolution that is resolve domain name into IP address and vice versa. As to remember IP addresses for every website is a difficult task so DNS work exactly same like checking phone numbers for a person name in the telephone directory. When a user enters a website address (URL) into the address bar, the DNS resolver takes 20 to 120 milliseconds to resolve the hostname into the IP address. Browser cannot download anything from the hostname until the DNS resolving process is completed. To speed up the process of DNS Resolution, DNS lookups (Forward lookups, Reverse Lookups) are cached for the better performance. Internet caching Server is the option which can be installed either locally (LAN) or installed by the Internet Service Provider. Following are ways that internet caching can be done to speed up the DNS Resolution process.INDEX
WAY
DESCRIPTION
1.
Caching on the Individuals Computer DNS information is stored on every individual’s computer via DNS Client Service (Microsoft Windows) into the Operating System cache.2.
Browsers Cache
Many of the browsers allow for storing cache, As long as the cached data is remain inside the browser there is no need to consult WindowCache.
3.
Microsoft Internet Explorer Browser Cache IE Caches DNS lookup for 30 mins (By default). The settings can be modified by the “DNSCacheTimeout” in theRegistry Settings
4.
Mozilla Firefox Browser Firefox caches DNS lookups for 1 mins. The settings can be changed via “network.dnsCacheExpiration” and can be enhanced up to 1 hour. When the Browser & the Computer DNS cache are empty, the DNS lookups will be equal to the unique host names in a web page. And the number of sources that contain host names are as mentionedbelow:
* Page Urls
* Style sheets
* Flash Objects
* Script Files
* Images
So always try to reduce the number of host names which in turns reduces the number of DNS lookups and as a result it improves the response time of the website.3. AVOID REDIRECTS
URL Redirection is the technique used for making the web page available under many URL’s. Moreover URL redirection is accomplished using 301 & 302 status code. Consider the following example of http headers in a 301 Response: _HTTP/1.1 301 Moved Permanently_ _Location: http://example1.com/newuri_ _Content-Type: text/html_ URL redirection can be implemented for the following reasons: * Due to user typing mistakes for example if the domain is example.com, but user mistakenly type for “exampel.com” or “exemple.com” so he is redirected to the correct domain. * If the website has changed from old to the new domain address, here we can use URL redirection concept. * Search engines usually have the record of old URL address and it might be possible that in few years your URL address has changed, but when user comes from Search engine, he get the old URL, in this situation URL redirection is used. Inspite of above mentioned reasons, it is not recommended to use URL Redirect because it slowdowns the user’s experience. 4. REDUCE COOKIE SIZE Cookie is a piece of code that resides in the user’s computer and is used to save the important information about the user. For example few websites take personal information of a user on each visit to a website. When we click on “save for the next time”, the information is stored on the client’s pc as a cookie. So http cookie is stored either for the personalization or authentication. But there are few important considerations while storing a cookie for a website (which are beneficial in improving the response time of the website): * Remove unnecessary Cookies * Make your cookie size as low as possible. * Place cookie at the appropriate domain level, so that it may not affect the other sub domains. * Set cookie valid expiry date. 5. PUT STYLE SHEETS AT THE TOP Following are the necessary points for placing style sheets at thetop:
* It is recommended that style sheets are needed to be placed at the top of the html documents because it helps in rendering html in theprogressive manner.
* As internet users might have slow internet connection so they are required any visual feedback like a progress bar in percentage, but in our case html page is the progress indicator itself, because if we use to place our CSS at the top of the html page (in the head section), our html page will render in the progressive manner. * But if you place at the bottom of the page, it is expected that you will not get the fine page loading or either you will see the white blank page, just because of the reason mostly browsers do not render html in which CSS is placed at the bottom of the page. 6. USE GET FOR AJAX REQUEST There are two ways of submitting Html form. These ways are dependent on the Form attribute called Method which has two values, one is Getand other is Post.
METHOD = GET:
GET is the default method of posting the Form and used when there is requirement of getting/retrieving data.METHOD = POST:
Whereas POST is used when there is a requirement of storing or updating data and/or ordering a product or sending an email. And post is the encoding way of sending values to the web server. RECOMMENDATION OF USING AJAX It is recommended that when you use XMLHttpRequest, always go for Get Method. Because Post is two way process while Get takes only one tcp packets to send. The maximum length of a URL is 2k in IE, after that you will not be able to use GET. Method Get is meant for retrieving data, so use Get when you are only requesting any information from Server. 7. MAKE JAVASCRIPT AND CSS AS AN EXTERNAL FILE CSS and JavaScript files should be used externally because it gives the benefit of improving response time of the website. * The reason is if you use JavaScript or CSS file externally, the browser usually caches these files and when user requests for the website, it renders the html in small size with less http Request (Due to the Browser Cache). * But if we use inline JavaScript or CSS file, these files are downloadable every time when users request for the website, thus it increases the size of the html page with less http requests (bydefault).
8. MINIMIZE DOM ACCESS Dom stands for Document Object Model. With the help of Dom you can access every piece of html. But it is recommended that our web page must have lower amount of DOM elements. In other words a complex web page means more bytes to download; also it means slower DOM access viaJavaScript.
In order to check your DOM elements you can use command in the Mozilla firebug add-one as mentioned below: _Document.getElementByID(‘*’).length_ For the optimize use of html elements you should compare your home page with the busiest page like Yahoo which is still under 700 htmlelements.
9. OPTIMIZE IMAGES
* Images are the important part of the website and thus are required to optimize before placing into the website. * It is not common that everybody have a high speed internet connection, in order to improve the response time for every user; Images need to be optimized accordingly. * Try to convert GIF into PNG. Mostly designers hesitate to using PNG Images because of the reason that it is not supported by majority browsers but it was the matter of past. * See your GIF images if they are using palette size corresponding to the no of colors in the image. * You can use imagemagick its easy to check with: Identify -verbose image.gif * There is a room for improvement when you see an image with 4 colors and a 256 color slots in the palette. 10. KEEP COMPONENTS UNDER 25K After the implementation of web 2.0, everybody likes to use web with their mobile phones, so you as a web designer or developer should optimized your website for the mobile phones. I Phone do not cache WebPages more than a size 25K. (Note that it is the uncompressed size). Here minification is important because gzip alone is not only the way to compress.CONCLUSION
One of the main issues on the Internet is, still, website loading speed. So with the above mentioned practices you may get benefited for your website or page loading speed. Posted by TheInfoTechWizard at 10:4337 comments
Email This
BlogThis!
Share
to Twitter
Share
to Facebook
Share
to Pinterest
10 TOOLS TO SPICE YOUR UNIX SHELL SCRIPTS There are some misconceptions that shell scripts are only for a CLI environment. You can easily use various tools to write GUI and/or network (socket) scripts under KDE or Gnome desktops. Shell scripts can make use of some of the GUI widget (menus, warning boxs, progress bars etc). You can always control the final output, cursor position on screen, various output effects, and so on. With the following tools you can build powerful, interactive, user friendly UNIX / Linux bashshell scripts.
#1: notify-send Command Creating GUI application is not just expensive task but task that takes time and patience. Luckily, both UNIX and Linux ships with plenty of tools to write beautiful GUI scripts. The following tools are tested on FreeBSD and Linux operating systems but should work under other UNIX like operating systems. The notify-send command allows you to send desktop notifications to the user via a notification daemon from the command line. This is useful to inform the desktop user about an event or display some form of information without getting in the user's way. You need to install the following package: $ sudo apt-get install libnotify-binIn this example, send simple desktop notification from the command line, enter: notify-send "rsnapshot done :)"Sample outputs:
Fig:01: notify-send in actionHere is another code with additionaloptions:
....
alert=18000
live=$(lynx --dump http://money.rediff.com/ | grep 'BSE LIVE' | awk '{ print $5}' | sed 's/,//g;s/\.*//g') && && { notify-send -t 5000 -u low -i "BSE Sensex touched 18k"; notify_counter=1; }...
Sample outputs:
Fig.02: notify-send with timeouts and other optionsWhere, * -t 5000: Specifies the timeout in milliseconds ( 5000 milliseconds= 5 seconds)
* -u low : Set the urgency level (i.e. low, normal, or critical). * -i gtk-dialog-info : Set an icon filename or stock icon to display (you can set path as -i /path/to/your-icon.png). For more information on use of the notify-send utility, please refer to the notify-send man page, viewable by typing man notify-send fromthe command line:
man notify-send
#2: TPUT COMMAND
The tput command is used to set terminal features. With tput you canset:
* Move the cursor around the screen. * Get information about terminal. * Set colors (background and foreground).* Set bold mode.
* Set reverse mode and much more. Here is a sample code:#!/bin/bash
# clear the screentput clear
# Move cursor to screen location X,Y (top left is 0,0)tput cup 3 15
# Set a foreground colour using ANSI escapetput setaf 3
echo "XYX Corp LTD."tput sgr0
tput cup 5 17
# Set reverse video modetput rev
echo "M A I N - M E N U"tput sgr0
tput cup 7 15
echo "1. User Management"tput cup 8 15
echo "2. Service Management"tput cup 9 15
echo "3. Process Management"tput cup 10 15
echo "4. Backup"
# Set bold mode
tput bold
tput cup 12 15
read -p "Enter your choice " choicetput clear
tput sgr0
tput rc
Sample outputs:
Fig.03: tput in action For more detail concerning the tput command, see the following manpage:
man 5 terminfo
man tput
#3: SETLEDS COMMAND
The setleds command allows you to set the keyboard leds. In this example, set NumLock on:setleds -D +num
To turn it off NumLock, enter:setleds -D -num
* -caps : Clear CapsLock. * +caps : Set CapsLock. * -scroll : Clear ScrollLock. * +scroll : Set ScrollLock. See setleds command man page for more information and options:man setleds
#4: ZENITY COMMAND
The zenity commadn will display GTK+ dialogs box, and return the users input. This allows you to present information, and ask for information from the user, from all manner of shell scripts. Here is a sample GUI client for the whois directory service for given domain name:#!/bin/bash
# Get domain name _zenity="/usr/bin/zenity" _out="/tmp/whois.output.$$" domain=$(${_zenity} --title "Enter domain" \ --entry --text "Enter the domain you would like to see whois info" )if
then
# Display a progress dialog while searching whois database whois $domain | tee >(${_zenity} --width=200 --height=100 \ --title="whois" --progress \ --pulsate --text="Searching domain info..." \ --auto-kill --auto-close \ --percentage=10) >${_out} # Display back output ${_zenity} --width=800 --height=600 \ --title "Whois info for $domain" \ --text-info --filename="${_out}"else
${_zenity} --error \ --text="No input provided"fi
Sample outputs:
Fig.04: zenity in Action See the zenity man page for more information and all other supportsGTK+ widgets:
zenity --help
man zenity
#5: KDIALOG COMMAND
kdialog is just like zenity but it is designed for KDE desktop / qt apps. You can display dialogs using kdialog. The following will display message on screen: kdialog --dontagain myscript:nofilemsg --msgbox "File: '~/.backup/config' not found."Sample outputs:
Fig.05: Suppressing the display of a dialog See shell scripting with KDE Dialogstutorial
for more information.#6: DIALOG
Dialog is an application used in shell scripts which displays text user interface widgets. It uses the curses or ncurses library. Here isa sample code:
>#!/bin/bash
dialog --title "Delete file" \ --backtitle "Linux Shell Script Tutorial Example" \ --yesno "Are you sure you want to permanently delete \"/tmp/foo.txt\"?" 7 60 # Get exit status # 0 means user hit button. # 1 means user hit button. # 255 means user hit key.response=$?
case $response in
0) echo "File deleted.";; 1) echo "File not deleted.";; 255) echo " key pressed.";;esac
See the dialog man page for details:man dialog
A NOTE ABOUT OTHER USER INTERFACE WIDGETS TOOLS UNIX and Linux comes with lots of other tools to display and control apps from the command line, and shell scripts can make use of some of the KDE / Gnome / X widget set: * GMESSAGE - a GTK-based xmessage clone. * XMESSAGE - display a message or query in a window (X-based/bin/echo)
* WHIPTAIL - display dialog boxes from shell scripts * PYTHON-DIALOG - Python module for making simple Text/Console-modeuser interfaces
#7: LOGGER COMMAND
The logger command writes entries in the system log file such as /var/log/messages. It provides a shell command interface to the syslogsystem log module:
logger "MySQL database backup failed." tail -f /var/log/messages logger -t mysqld -p daemon.error "Database Server failed" tail -f /var/log/syslogSample outputs:
Apr 20 00:11:45 vivek-desktop kernel: CPU0: Temperature/speed normal Apr 20 00:12:20 vivek-desktop mysqld: Database Server failed See howto write message to a syslog / log filefor
more information. Alternatively, you can see the logger man page fordetails:
man logger
#8: SETTERM COMMAND
The setterm command can set various terminal attributes. In this example, force screen to turn black in 15 minutes. Monitor standby will occur at 60 minutes: setterm -blank 15 -powersave powerdown -powerdown 60 In this example show underlined text for xterm window: setterm -underline on; echo "Add Your Important Message Here" setterm -underline off Another useful option is to turn on or off cursor: setterm -cursor offTurn it on:
setterm -cursor on See the setterm command man page for details:man setterm
#9: SMBCLIENT: SENDING MESSAGES TO MS-WINDOWS WORKSTATIONS The smbclient command can talk to an SMB/CIFS server. It can send a message to selected users or all users on MS-Windows systems: smbclient -M WinXPPro <Details
Copyright © 2024 ArchiveBay.com. All rights reserved. Terms of Use | Privacy Policy | DMCA | 2021 | Feedback | Advertising | RSS 2.0